Demystifying the 5 Stages of Ethical Hacking
In a world where cyber threats are becoming increasingly sophisticated, ethical hacking has emerged as a critical practice for organizations aiming to protect their digital assets. Also known as penetration testing, ethical hacking involves simulating cyber attacks to identify and mitigate vulnerabilities before they can be exploited by malicious actors. Let’s demystify the five stages of ethical hacking and understand how they work together to strengthen cybersecurity.
If you want to excel in this career path, then it is recommended that you upgrade your skills and knowledge regularly with the latest Ethical Hacking Course in Bangalore.

1. Planning and Reconnaissance
The first stage of ethical hacking is all about preparation and information gathering. This phase consists of two primary activities:
-
Passive Reconnaissance: This involves collecting information from publicly available resources, such as social media, websites, and domain registries, without the target's direct involvement. The aim is to gather as much background data as possible.
-
Active Reconnaissance: In this approach, ethical hackers interact directly with the target’s systems to discover live hosts, open ports, and services running on those ports. This step is crucial for building a comprehensive profile of the target.
The goal of this stage is to identify potential entry points for a future attack.
2. Scanning
Once the reconnaissance phase is complete, the next step is scanning. This stage involves utilizing various tools to analyze the target’s network and systems. Key techniques include:
-
Network Scanning: Identifying all active devices on the network.
-
Port Scanning: Checking which ports are open and what services are associated with them.
-
Vulnerability Scanning: Using automated tools to identify known vulnerabilities in the systems.
This phase helps ethical hackers gain insight into the target's security posture and highlight areas that need attention.
3. Gaining Access
With a clear understanding of the target’s vulnerabilities, ethical hackers move to the gaining access phase. This stage involves exploiting identified weaknesses to gain unauthorized access. Techniques may include:
-
Exploiting Vulnerabilities: Launching attacks that target specific flaws in software or hardware.
-
Social Engineering: Manipulating individuals into revealing sensitive information, such as passwords or confidential data.
The objective here is to demonstrate how an attacker could breach the system and access sensitive information.
With the aid of Ethical Hacking Online Training programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.
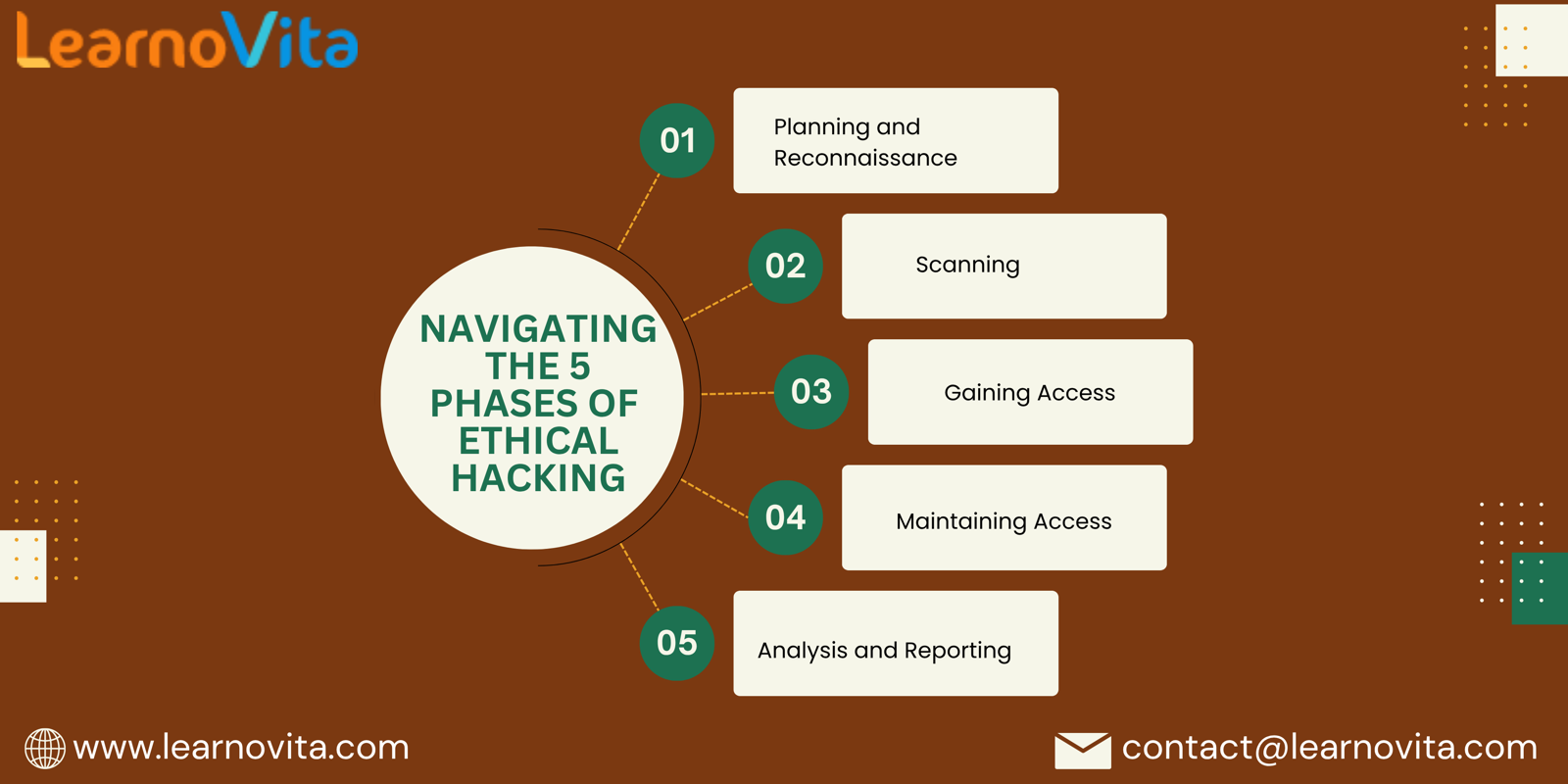
4. Maintaining Access
After successfully breaching a system, the focus shifts to maintaining access. This phase is essential for understanding how long an attacker could remain undetected within a system. Key activities include:
-
Creating Backdoors: Implementing tools that allow continued access even if the initial vulnerabilities are patched.
-
Privilege Escalation: Gaining higher levels of access to enhance control over the system.
This stage emphasizes the risks posed by undetected breaches and the importance of continuous monitoring.
5. Analysis and Reporting
The final stage is about compiling the findings into a structured report that provides actionable insights. This report typically includes:
-
Summary of Findings: A detailed overview of all vulnerabilities discovered during the assessment.
-
Recommendations: Suggested remediation strategies to address the identified issues.
-
Risk Assessment: Evaluating the potential impact of each vulnerability on the organization.
This phase is crucial for organizations to understand their security posture and implement necessary changes to bolster their defenses.
Conclusion
Ethical hacking is an invaluable practice in today’s digital landscape. By following these five stages—planning and reconnaissance, scanning, gaining access, maintaining access, and analysis and reporting—organizations can effectively identify and mitigate vulnerabilities. Embracing ethical hacking not only protects sensitive information but also strengthens overall security, making it a fundamental component of any robust cybersecurity strategy.

Comments
Post a Comment