Understanding the Significance of Identity Access Management: CyberArk's Impact on Security Solutions

What Is Identity Access Management (IAM)?
Identity Access Management (IAM) encompasses the processes and technologies organizations utilize to oversee digital identities and manage access to information. The primary goal of IAM is to ensure that the right individuals can access the right resources at the appropriate times for legitimate reasons.
Key Components of IAM
-
User Identification: Assigning unique identifiers to all users in the organization.
-
Authentication: Verifying user identities using methods such as passwords, biometrics, or multi-factor authentication.
-
Authorization: Controlling access based on user roles and permissions.
-
User Lifecycle Management: Managing user accounts throughout their lifecycle, from creation to termination.
-
Monitoring and Reporting: Tracking user activity and generating reports to pinpoint potential security threats.
The Importance of IAM
IAM is vital for a variety of reasons:
- Improved Security: By regulating access to sensitive data and systems, IAM prevents unauthorized entries and data breaches.
- Regulatory Compliance: Many industries are required to follow strict regulations that mandate effective IAM practices.
- Operational Efficiency: Streamlined IAM processes reduce IT workloads and minimize human error.
- Enhanced User Experience: Features like Single Sign-On (SSO) simplify access to multiple applications, improving user satisfaction.
CyberArk’s Role in Enhancing IAM
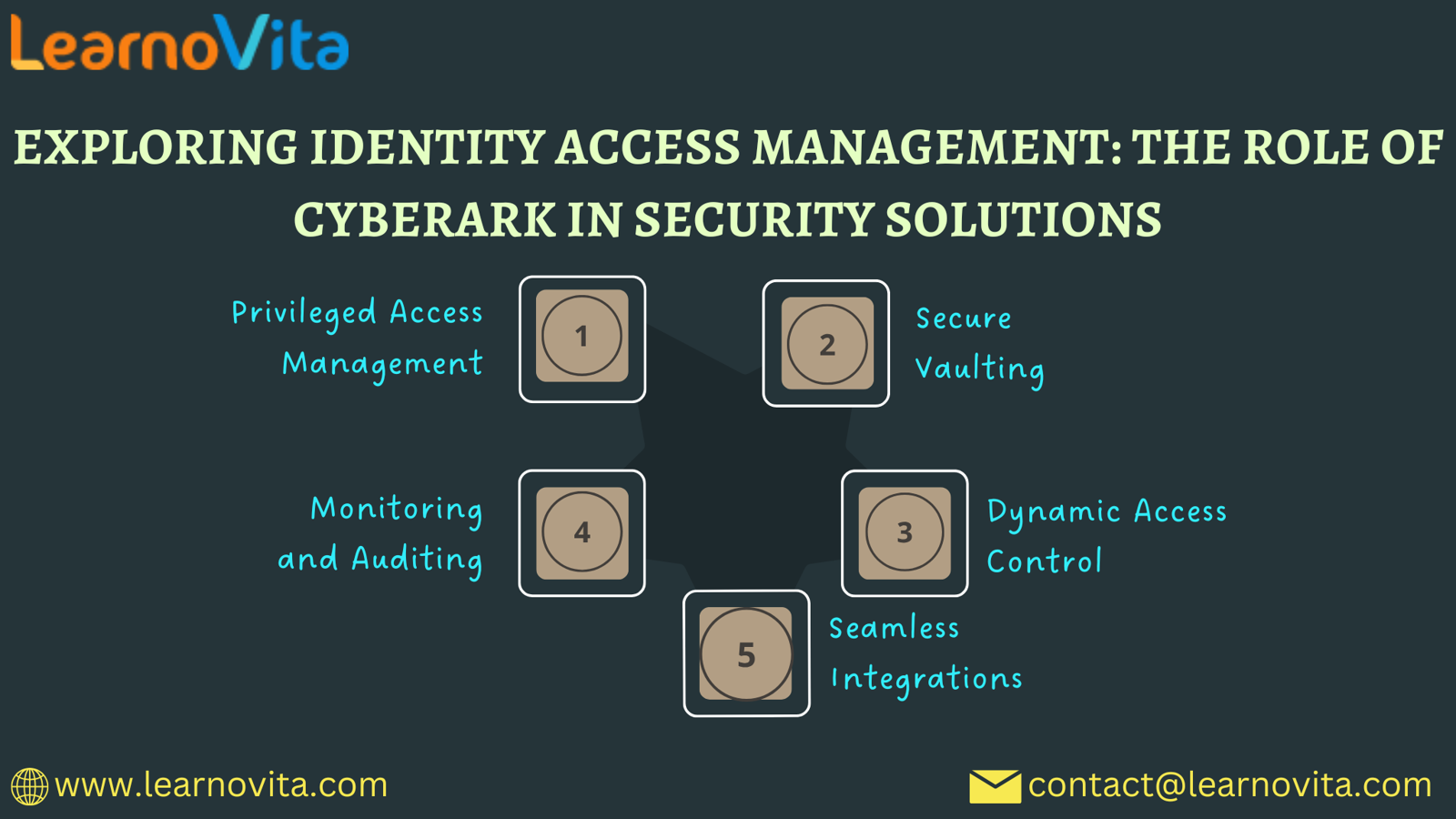
CyberArk is a recognized leader in privileged access management (PAM) and significantly strengthens IAM frameworks in organizations. Here’s how CyberArk contributes:
1. Securing Privileged Accounts
CyberArk focuses on managing privileged accounts, which have elevated access rights. Securing these accounts mitigates the risks associated with credential theft—one of the primary threats in cybersecurity.
2. Secure Credential Management
CyberArk offers a secure vault for storing sensitive credentials, ensuring that only authorized personnel have access. This safeguards against unauthorized credential usage.
3. Dynamic Access Control
With CyberArk, organizations can implement dynamic access controls that adjust according to user behavior and risk profiles. This adaptability facilitates quicker responses to potential threats.
4. Comprehensive Monitoring Capabilities
CyberArk provides extensive monitoring tools that oversee user activities, generating alerts for any unusual patterns. This proactive monitoring aids in identifying and addressing threats before they escalate.
5. Effortless Integration
CyberArk is designed to seamlessly integrate with existing IAM solutions, enhancing their functionality without the need for a full system overhaul. This interoperability allows organizations to maximize their security investments.
Conclusion
Identity Access Management is a crucial element of a comprehensive security strategy. In light of the increasing complexity of cyber threats, integrating strong solutions like CyberArk is essential for bolstering IAM practices. By effectively securing privileged accounts and managing access, CyberArk supports organizations in maintaining a robust security posture.
As businesses adapt to the demands of the digital age, prioritizing IAM while leveraging powerful tools like CyberArk ensures that security remains a top concern. Protecting an organization’s most valuable asset—its data—requires a forward-thinking approach, with IAM at the core.

Comments
Post a Comment