Securing Cloud Infrastructures: How CyberArk Enhances Protection
- Get link
- X
- Other Apps

Navigating the Cloud Security Challenges
The shift to cloud infrastructures often leaves traditional security measures inadequate. While the cloud fosters dynamic collaboration and access, it also brings vulnerabilities, especially concerning privileged accounts. CyberArk addresses these risks, focusing on safeguarding these critical access points to ensure security and compliance.
CyberArk's Vital Cloud Security Features
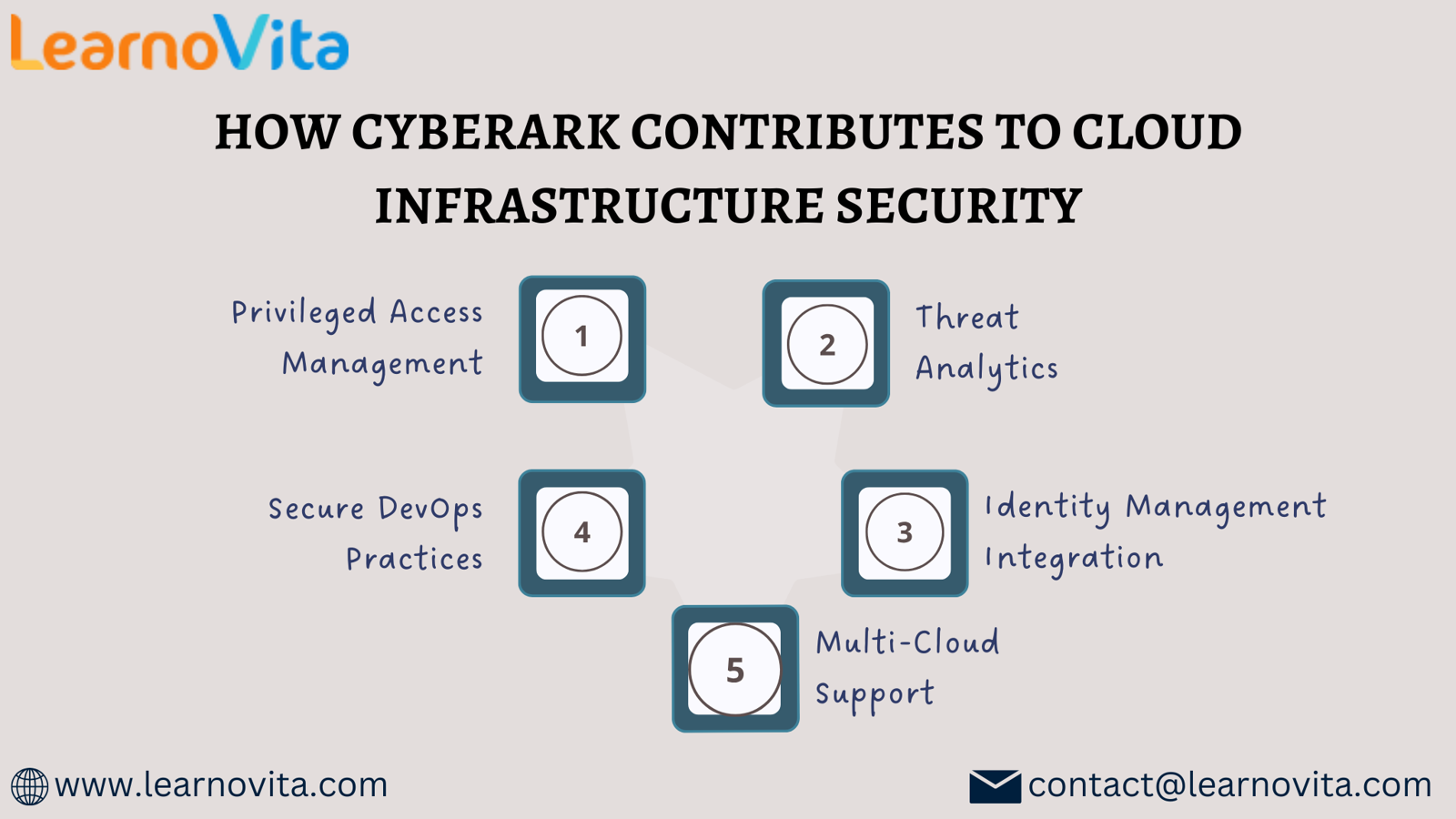
1. Privileged Access Management
Privileged accounts are essential for accessing sensitive systems and data. CyberArk’s PAM solutions empower organizations to manage and monitor these accounts effectively, featuring:
- Session Recording and Monitoring: This enables auditing and ensures review capability for privileged user actions.
- Automatic Credential Rotation: CyberArk automates credential rotation to mitigate the risk of theft and maintain secure access.
2. Threat Analytics
With powerful analytics capabilities, CyberArk detects and addresses anomalies in real time. Utilizing machine learning, it identifies suspicious activities—such as unusual logins—and enables rapid response to potential threats.
3. Identity Management Integration
CyberArk integrates smoothly with existing identity management systems, strengthening access control. This ensures that user identities are verified, while only authenticated individuals receive access, thereby reducing unauthorized access risks.
4. Support for Secure DevOps Practices
As organizations embrace DevOps methodologies in cloud environments, CyberArk aids in managing credentials used in automation, preventing hard-coded secrets in application code and fostering secure development practices without compromising agility.
5. Multi-Cloud Compatibility
Advantages of Implementing CyberArk
1. Strengthened Security Posture
By concentrating on privileged account protection, CyberArk helps organizations minimize their attack surface, enhancing their overall security posture, which is vital for cloud adoption.
2. Support for Compliance Needs
Compliance with regulations is crucial for many organizations. CyberArk facilitates adherence by providing detailed audit trails and comprehensive reporting capabilities.
3. Increased Operational Efficiency
Automating privileged account management allows IT teams to focus on higher-value tasks, increasing efficiency and reducing workload.
4. Scalability and Flexibility
CyberArk's solutions are designed for scalability, easily accommodating organizational growth without compromising security.
Conclusion
As more organizations embrace cloud technologies, robust security solutions are essential. CyberArk plays a crucial role in protecting cloud-based infrastructures through its sophisticated privileged access management, threat detection, and compliance support. By choosing CyberArk, organizations not only safeguard their sensitive information but also foster a secure and effective cloud strategy.
For businesses aiming to enhance their cloud security, CyberArk provides the expertise and tools necessary to navigate the complexities of cloud environments with confidence.
- Get link
- X
- Other Apps

Comments
Post a Comment